On becoming an expert C programmer →
The following is from an EMail message that I sent to to an individual on 12-Apr-2001. You may find this EMail message useful.
The Writer asked:
``I just recently visited your website … Just wanted to say greetings and ask a simple question: Do you think I stand a chance in the C programming field if I keep it up? Tell me what I should do in order to keep strong feelings towards C.''
Yet Another Hex Word
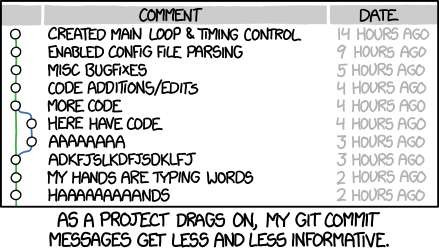
How to Write a Git Commit Message →
The seven rules of a great git commit message
zsh: no matches found →
With the use of Git or Octopress (typically Rake), we type
[,],^characters to terminal:git reset HEAD^rake install[classic]Some Zsh users know what would happen when we type that commands:
zsh: no matches found: HEAD^zsh: no matches found: install[classic]This is caused by Zsh:
zsh allows Filename Generation and Pattern Matching (Globbing) using square brackets and other characters (explained in the zsh guide, section 5.9).
The solution is simple:
The solution, found in the zsh FAQ (section 3.4), is simply adding a line in ~/.zshrc that disables globbing for a single command:
alias rake="noglob rake"Aliasing
gitis also useful:alias git="noglob git"Undocumented iOS functions allow monitoring of personal data, expert says →
“Backdoor” can be abused by gov’t agents and ex-lovers to gain persistent access.
Apple has endowed iPhones with undocumented functions that allow unauthorized people in privileged positions to wirelessly connect and harvest pictures, text messages, and other sensitive data without entering a password or PIN, a forensic scientist warned over the weekend.
Zdziarski said the service that raises the most concern is known as com.apple.mobile.file_relay. It dishes out a staggering amount of data—including account data for e-mail, Twitter, iCloud, and other services, a full copy of the address book including deleted entries, the user cache folder, logs of geographic positions, and a complete dump of the user photo album—all without requiring a backup password to be entered. He said two other services dubbed com.apple.pcapd and com.apple.mobile.house_arrest may have legitimate uses for app developers or support people but can also be used to spy on users by government agencies or even jilted ex-lovers. The Pcapd service, for instance, allows people to wirelessly monitor all network traffic traveling into and out of the device, even when it’s not running in a special developer or support mode. House_arrest, meanwhile, allows the copying of sensitive files and documents from Twitter, Facebook, and many other applications.
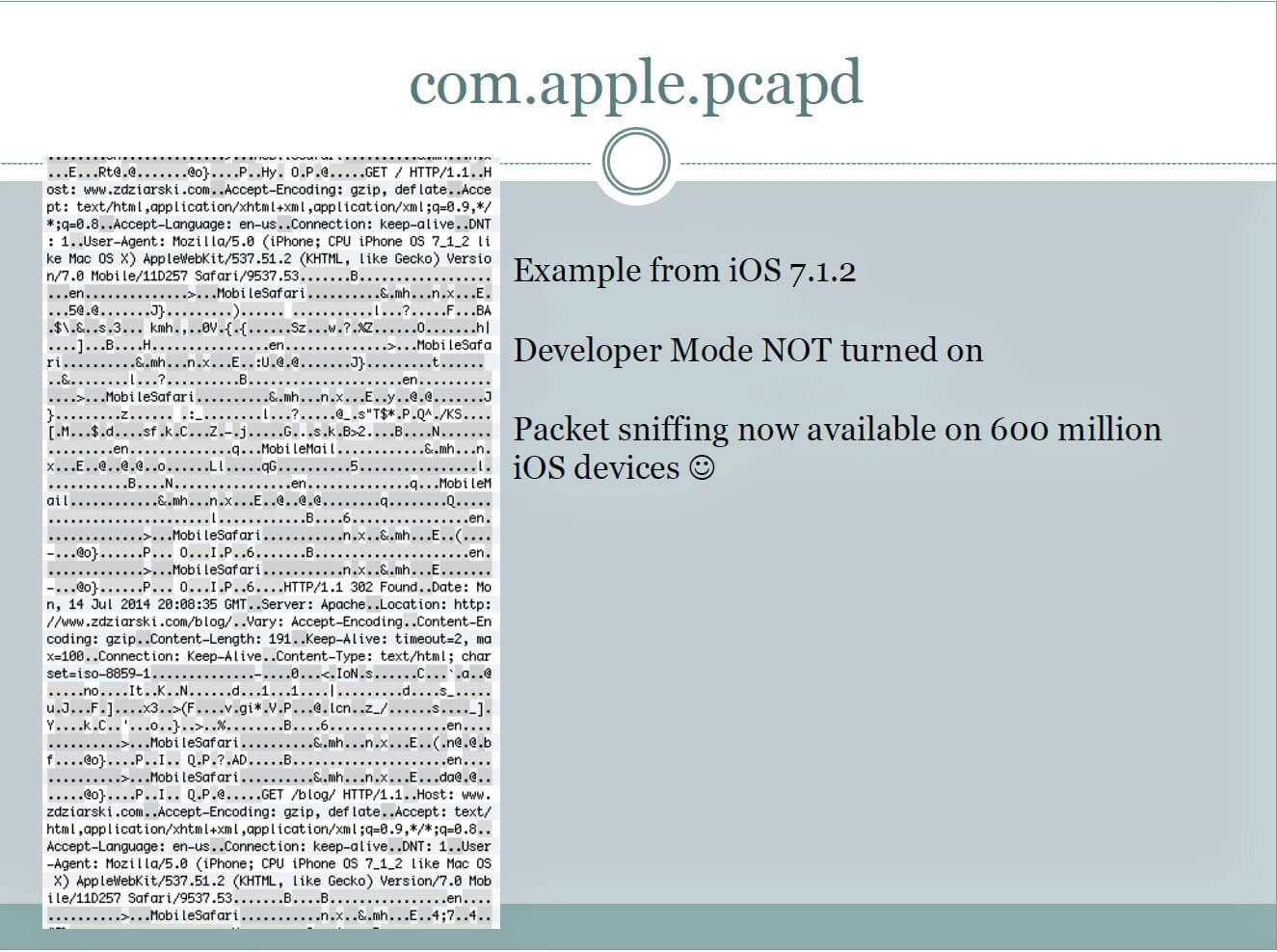
Slides of Zdziarski’s talk, titled Identifying Back Doors, Attack Points, and Surveillance Mechanisms in iOS Devices are here.
Also check the page about iOS: About diagnostic capabilities on Apple Support:
Each of these diagnostic capabilities requires the user to have unlocked their device and agreed to trust another computer. Any data transmitted between the iOS device and trusted computer is encrypted with keys not shared with Apple. For users who have enabled iTunes Wi-Fi Sync on a trusted computer, these services may also be accessed wirelessly by that computer.